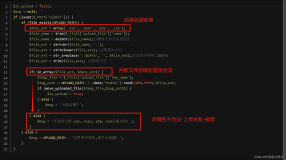
cRARk is a .rar archive password cracker, but unlike rarcrack, can be customised to a far greater extent to allow partial passwords, wordlists, complementing wordlists with characters and more.
Also this programme is CUDA enabled which allows for a vast increase in testing speed.
This of course only if you have a capable graphics card. ( http://www.nvidia.com/object/cuda_gpus.html)
cRARk is not installed by default on BT4 Final, a shame really as it is more versatile than rarcrack in my opinion. To install it though is a piece of cake ;
! During the install, the program tried to install the CUDA dependacies as well, in order for this to work properly you will need to exit 'X'. To do this press Ctrl + Del + Backspace to get back into Command Line only.
So seems best way to install is to get online, then quit X with Ctrl + Del + Backspace, and then run the apt-get install from the command line interface.
The machine I installed it onto does not have any CUDA capabilities, so this post will only go through some of the functions of cRARk without testing the CUDA improvements on cracking speed.
I may later try to do a full HDD install on my desktop to see if I can get my 8800GTS to work.
So after installing cRARk, lets fire it up through either the menu;
Lets check out the files the readme's and what general options are advised;
To start off we need to create the password.def file. To do this simply copy either the english.def file or the crackme.def file to password.def ;
Then to modify the password.def file to reflect the options we want to use.
Here I will be working with simple password protected files stored on my flashdrive (mounted on /media/8GB/)
Testing password protected test100.rar file with password 100 ;
As my system cannot use CUDA I will disable it with the -c command when testing.
For checking password protected testabc.rar file with lowercase letters only ;
./crark -c /media/8GB/testabc.rar
For checking a password protected test-ABC.rar with uppercase characters only ;
./crark -c /media/8GB/test-ABC.rar
To check all of the above on password protected testaB1.rar ;
./crark -c /media/8GB/testaB1.rar
To go all out and also include special characters ;
To test the password.def file and see whether the commands are going to work OK, the programme can test run the definitions using the -v option ;
This wont actually start the cracking process, but will print the characters on screen so you can check whether its doing what you want it to.
To specify the number of characters, the options -l & -g can be used.
So to specify a minimum of 3 characters and a maximum of 5 characters;
The bruteforce attempts resulted in an average of around 60 pass/sec on my netbook and around 160 pass/sec on my desktop (windows version of cRARk).
With CUDA this will be greatly enhanced, but have to see if/when I can get that going.
cRARk also has the option to check passwords from a wordlist file.
To do this the password.def file needs to be adjusted to specify the location of the wordlist with $w, in this case I have copied a small english wordlist called english.dic into cRARk's directory.
(You can of course also specify an alternative location where the wordlist is)
Then we need to specify that cRARk will use a wordlist in password.def ;
The dictionary attacks averaged around 20 pass/sec on my netbook and I understand that there is no CUDA support for the dictionary attacks..
So having a focussed wordlist is a must !
To allow an easier choice of options, it is also possible to prepare some definition files and then specify these with the -p option.
For instance you can prepare a .def file which will use a wordlist file as follows and then keep there for future use ;
cp password.def wordlist.def
Then to specify to use the newly created wordlist.def file, the -p option is included ;
There are a huge number of options to play with when it comes to the wordlist usage, extra options can be included to capitalize / invert / mashup / add numbers etc etc etc
I may update the post to show some of these options on a test wordlist.
It will be interesting to see how far I can get with the CUDA side of things, however that would mean a full HDD install on the desktop (doesnt work in VMware).
ADVANCED DICTIONARY OPTIONS
Following some queries in the comments I got to checking how the wordlist and the wordlist
manipulations work.
It truly is fantastically (and terrifyingly) customizable..
If for instance you have a list of words and you know that the password is a combination
of a couple of these words, then you can tell crark to do that in the .def file as follows;
For 2 words from the wordlist in succession;
wordlist.def
$w = "wordlist.txt"
##
$w $w
For 3 words from the wordlist in succession;
wordlist.def
$w = "wordlist.txt"
##
$w $w $w
If you have 2 wordlists and you know that the password will be a combination of
words of the 2 lists (only 1 way, so words from 2nd list appended to words from 1st list for instance)
then you can identify the 2nd wordlist with the $u function ;
wordlist.def
$u = "wordlist1.txt"
$w = "wordlist2.txt"
##
$u $w
So in the above all words from wordlist2.txt will be suffixed/appended to each word in wordlist1.
And of course any number of combinations of the above can be made.
In the below example ;
wordlist.def
$w = "test1.txt"
$u = "test2.txt"
##
$u$w$u
Author's Helpfile & Linkage ;
http://www.crark.net/cRARk.html
or
http://www.youtube.com/watch?v=viYdoZiCYaA
Also this programme is CUDA enabled which allows for a vast increase in testing speed.
This of course only if you have a capable graphics card. ( http://www.nvidia.com/object/cuda_gpus.html)
cRARk is not installed by default on BT4 Final, a shame really as it is more versatile than rarcrack in my opinion. To install it though is a piece of cake ;
apt-get install crark
! During the install, the program tried to install the CUDA dependacies as well, in order for this to work properly you will need to exit 'X'. To do this press Ctrl + Del + Backspace to get back into Command Line only.
So seems best way to install is to get online, then quit X with Ctrl + Del + Backspace, and then run the apt-get install from the command line interface.
The machine I installed it onto does not have any CUDA capabilities, so this post will only go through some of the functions of cRARk without testing the CUDA improvements on cracking speed.
I may later try to do a full HDD install on my desktop to see if I can get my 8800GTS to work.
So after installing cRARk, lets fire it up through either the menu;
Start/Dragon --> Backtrack --> Privilage Escalation --> Password Attacks --> OfflineAttacks --> Crark
or command line ;
cd /pentest/passwords/crark/
Lets check out the files the readme's and what general options are advised;
ls
./crark
BRUTEFORCE ATTACKS
================
To start off we need to create the password.def file. To do this simply copy either the english.def file or the crackme.def file to password.def ;
cp crackme.def password.def
Then to modify the password.def file to reflect the options we want to use.
Here I will be working with simple password protected files stored on my flashdrive (mounted on /media/8GB/)
Testing password protected test100.rar file with password 100 ;
nano password.def
Under the double hash enter the testing methods desired, in this case as only numbers ;
[$1] *
Save and exit
As my system cannot use CUDA I will disable it with the -c command when testing.
./crark -c /media/8GB/test100.rar
For checking password protected testabc.rar file with lowercase letters only ;
nano password.def
[$a] *
Save and exit.
./crark -c /media/8GB/testabc.rar
For checking a password protected test-ABC.rar with uppercase characters only ;
nano password.def
[$A] *
Save and exit
./crark -c /media/8GB/test-ABC.rar
To check all of the above on password protected testaB1.rar ;
nano password.def
[$a $A $1] *
Save and exit
./crark -c /media/8GB/testaB1.rar
!! It is important to note that cRARk will start checking based on the same sequence as the characters are entered in the definition file.
So in the above example entering the character information in the definition file as $1 $a $A would take a lot longer to find the password then if using $a $A $1 .
The end result will be the same, cRARk will find the password, but the time needed for checking will be severely affected.
(I thought I had messed up somewhere earlier on when I changed character sequence in definition file and it took longer than previous attempts).
To go all out and also include special characters ;
nano password.def
[$a $A $1 $!] *
Save and exit.
To test the password.def file and see whether the commands are going to work OK, the programme can test run the definitions using the -v option ;
./crark -c -v /media/8GB/test100.rar
This wont actually start the cracking process, but will print the characters on screen so you can check whether its doing what you want it to.
To specify the number of characters, the options -l & -g can be used.
So to specify a minimum of 3 characters and a maximum of 5 characters;
./crark -c -l3 -g5 /media/8GB/testabc.rar
The bruteforce attempts resulted in an average of around 60 pass/sec on my netbook and around 160 pass/sec on my desktop (windows version of cRARk).
With CUDA this will be greatly enhanced, but have to see if/when I can get that going.
WORDLIST/DICTIONARY ATTACKS
======================
cRARk also has the option to check passwords from a wordlist file.
To do this the password.def file needs to be adjusted to specify the location of the wordlist with $w, in this case I have copied a small english wordlist called english.dic into cRARk's directory.
(You can of course also specify an alternative location where the wordlist is)
Then we need to specify that cRARk will use a wordlist in password.def ;
nano password.def
$w = "english.dic"
##
$w
Save and exit.
./crark -c /media/8GB/testAmsterdam.rar
The dictionary attacks averaged around 20 pass/sec on my netbook and I understand that there is no CUDA support for the dictionary attacks..
So having a focussed wordlist is a must !
To allow an easier choice of options, it is also possible to prepare some definition files and then specify these with the -p option.
For instance you can prepare a .def file which will use a wordlist file as follows and then keep there for future use ;
cp password.def wordlist.def
Then to specify to use the newly created wordlist.def file, the -p option is included ;
./crark -c -pwordlist.def /media/8GB/testAmsterdam.rar
There are a huge number of options to play with when it comes to the wordlist usage, extra options can be included to capitalize / invert / mashup / add numbers etc etc etc
I may update the post to show some of these options on a test wordlist.
It will be interesting to see how far I can get with the CUDA side of things, however that would mean a full HDD install on the desktop (doesnt work in VMware).
ADVANCED DICTIONARY OPTIONS
Following some queries in the comments I got to checking how the wordlist and the wordlist
manipulations work.
It truly is fantastically (and terrifyingly) customizable..
If for instance you have a list of words and you know that the password is a combination
of a couple of these words, then you can tell crark to do that in the .def file as follows;
For 2 words from the wordlist in succession;
wordlist.def
$w = "wordlist.txt"
##
$w $w
For 3 words from the wordlist in succession;
wordlist.def
$w = "wordlist.txt"
##
$w $w $w
If you have 2 wordlists and you know that the password will be a combination of
words of the 2 lists (only 1 way, so words from 2nd list appended to words from 1st list for instance)
then you can identify the 2nd wordlist with the $u function ;
wordlist.def
$u = "wordlist1.txt"
$w = "wordlist2.txt"
##
$u $w
So in the above all words from wordlist2.txt will be suffixed/appended to each word in wordlist1.
And of course any number of combinations of the above can be made.
In the below example ;
wordlist.def
$w = "test1.txt"
$u = "test2.txt"
##
$u$w$u
Author's Helpfile & Linkage ;
http://www.crark.net/cRARk.html
Video on the above ;
or
http://www.youtube.com/watch?v=viYdoZiCYaA